Tools Automated Threat Intelligent System integrated with McAfee Advanced Threat Defense and Malware Information Sharing Platform 02/09/2019 Anastasis Vasileiadis Automated Threat Intelligent System An improvised automated threat intelligent system with advanced vulnerability scanners and Opensource Intelligence Information gathering python scripts when integrated with McAfee Advanced Threat Defense and Malware Information Sharing Platform can defend against new and futuristic cyber attacks. ATD-MISP with OpenDXL This integration is focusing on the automated threat intelligence collection with McAfee ATD, OpenDXL, and MISP. McAfee Advanced Threat Defense (ATD) will produce local threat intelligence that will be pushed via DXL. An OpenDXL wrapper will subscribe and parse indicators ATD produced and will import indicators into a threat intelligence management platform (MISP). Component Description McAfee Advanced Threat Defense (ATD) ...
[BlackHat USA tool] Powershell-RAT: Python based backdoor Powershell-RAT
The python-based backdoor that uses Gmail to exfiltrate data through attachment. This RAT will help during the red team engagements to backdoor any Windows machines. It tracks the user activity using screen capture and sends it to an attacker as an e-mail attachment.
Note: This piece of code is Fully UnDetectable (FUD) by Anti-Virus (AV) software.
This project must not be used for illegal purposes or for hacking into the system where you do not have permission, it is strictly for educational purposes and for people to experiment with.
RAT Architecture Diagram
Setup
- git clone https://github.com/Viralmaniar/Powershell-RAT.git
- Throwaway Gmail email address
- Enable “Allow less secure apps” by going to https://myaccount.google.com/lesssecureapps
- Modify the $username & $password variable for your account in the Mail.ps1 Powershell file
- Modify $msg.From & $msg.To.Add with throwaway Gmail address
How do I use this?
- Press 1: This option sets the execution policy to unrestricted using
Set-ExecutionPolicy Unrestricted. This is useful on administrator machine - Press 2: This takes the screenshot of the current screen on the user machine using
Shoot.ps1Powershell script - Press 3: This option backdoors the user machine using
schtasksand sets the task name toMicrosoftAntiVirusCriticalUpdatesCore - Press 4: This option sends an email from the user machine using
Powershell. These usesMail.ps1file to send screenshot as attachment to exfiltrate data - Press 5: This option backdoors the user machine using
schtasksand sets the task name toMicrosoftAntiVirusCriticalUpdatesUA - Press 6: This option deletes the screenshots from user machine to remain stealthy
- Press 7: This option backdoors the user machine using
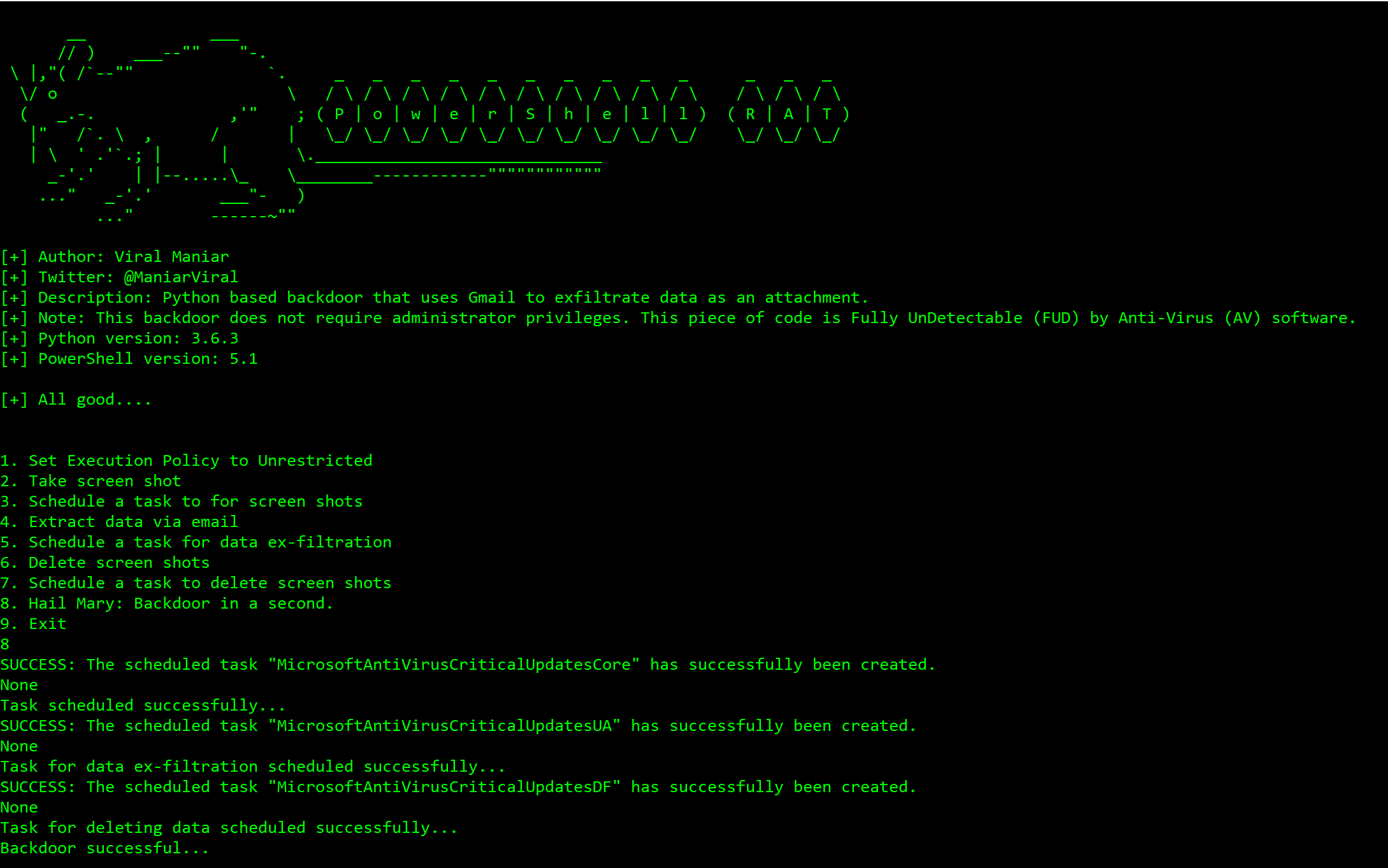
schtasksand sets the task name toMicrosoftAntiVirusCriticalUpdatesDF - Press 8: This option performs all of the above with a single button
press 8on a keyboard. Attacker will receive an email every5 minuteswith screenshots as an email attachment. Screenshots will be deleted after12 minutes - Press 9: Exit gracefully from the program or press
Control+C
On the first run of the
Powershell-RAT user will get options as below:
Using
Hail Mary option to backdoor a Windows machine:
Successfully taking screenshots of the user activity:
Data exfiltrated as an email attachment using Gmail:
Author: @ManiarViral
Source: https://github.com/Viralmaniar/


ความคิดเห็น
แสดงความคิดเห็น